How to Scan WordPress Database for Malware

We recently searched the internet for help on how to scan a WordPress database for malware but could not find any. We thus decided to examine how to do this and provide the solution to others who need help to scan their database.
If you are facing a malware infection on your website, it is also quite possible that your database has been infected too. And if this is the case, you may take steps to clean your site code and files of all malware but still find malware behavior in your site.
Gladly, there are steps you can take to confirm if your database is infected, identify the malware, and remove them from your WordPress site.
[thrive_2step id=’36527′]Remove your WordPress malware by professionals. Check our limited time offer here![/thrive_2step]
In this article:
Before You Scan Your WordPress Database
Before scanning your WordPress website database, you must have first scanned and cleaned your WordPress files of every trace of malware.
Malware enters into your database through injection codes in your WordPress files. If these files are not cleaned first, the code will simply inject new malware into your DB after you’re done cleaning.
You can clean your site files using a WordPress malware removal plugin.
You must also ensure your database and WordPress files are backed up. In the event that this goes wrong, you need to be able to restore your site. A malware infected site is better than no site at all – you can always remove malware.
If you have done the steps above, read on to learn how to scan WP database for malware.
Methods to Scan WordPress Database for Malware
First, because of the seriousness of a malware infection, we always recommend that you have an expert get you out of it. You may request our WordPress Malware Removal Service and we will clean your site and database of all malicious files and website malware.
However, if you have some technical knowledge and want to proceed, we will take you through the steps needed to rid your database of malware.
There are two methods to do this – 1. manual code search, and 2. scanning with a WordPress plugin.
Manual Code Search for Hidden Malware
Hackers use a set of known functions to exploit vulnerable WordPress Websites. You can search your database for these commonly used functions to see if they are present, which would suggest the presence of malware. Also, if your site is redirecting to spammy links, you should search your DB for these links as well.
Export Your DB SQL
To search your DB, you would need to export it as text. Using the database tool provided by your web host, you can perform this export. In this guide, we show you how to do this using PhpMyAdmin.
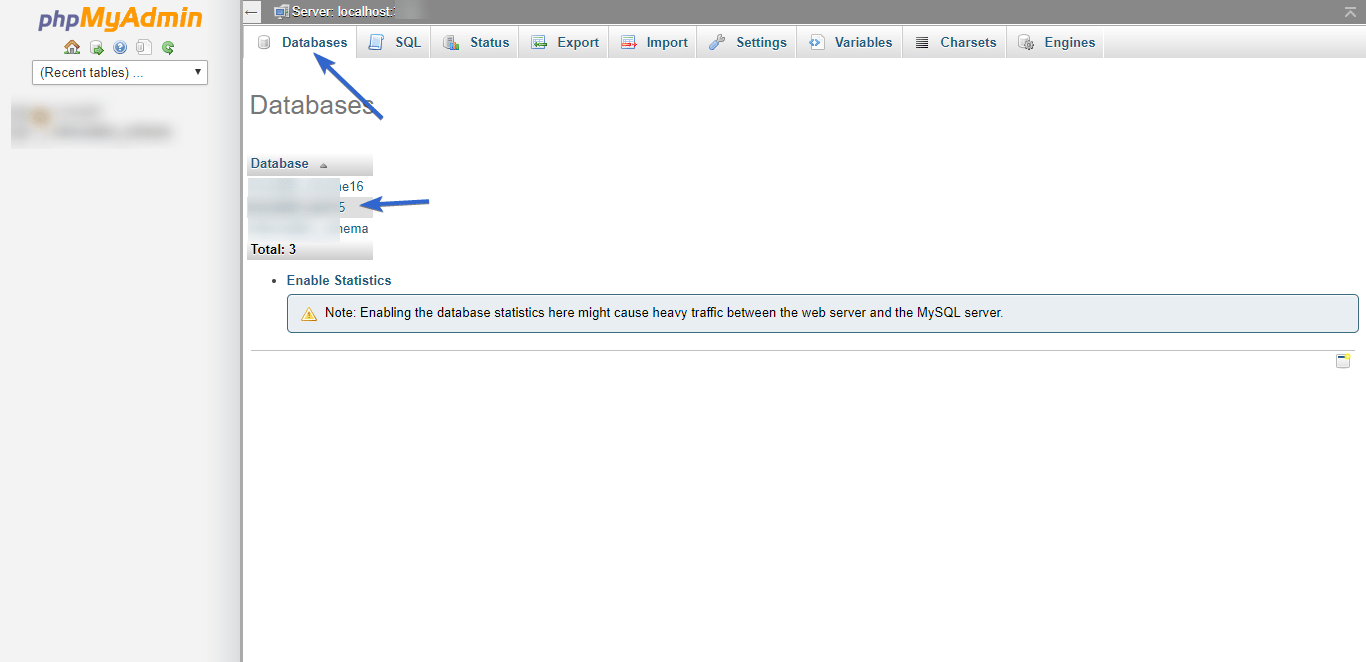
To get started, login to your cPanel dashboard, scroll to the “Databases” section and click PhpMyAdmin.
Select your WordPress database from the list on the left.
Next, click Export in the top menu.
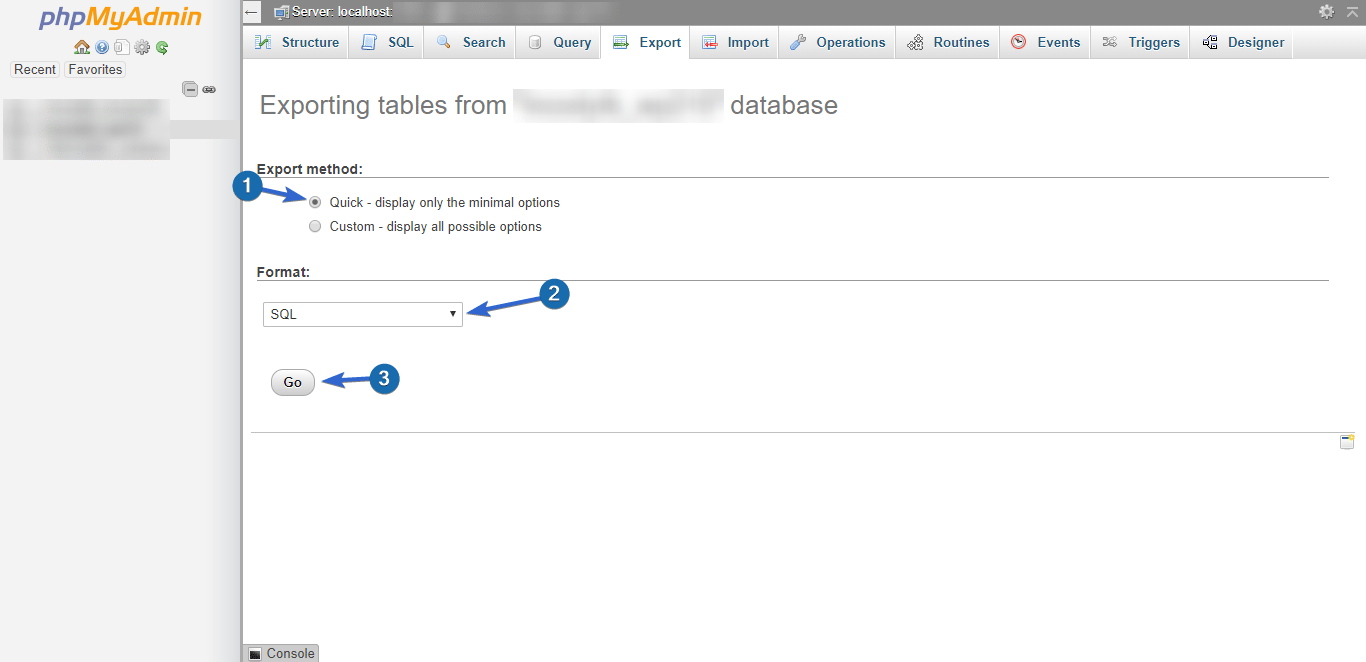
Leave the export method set to “Quick”, leave the format set to “SQL”, and click GO.
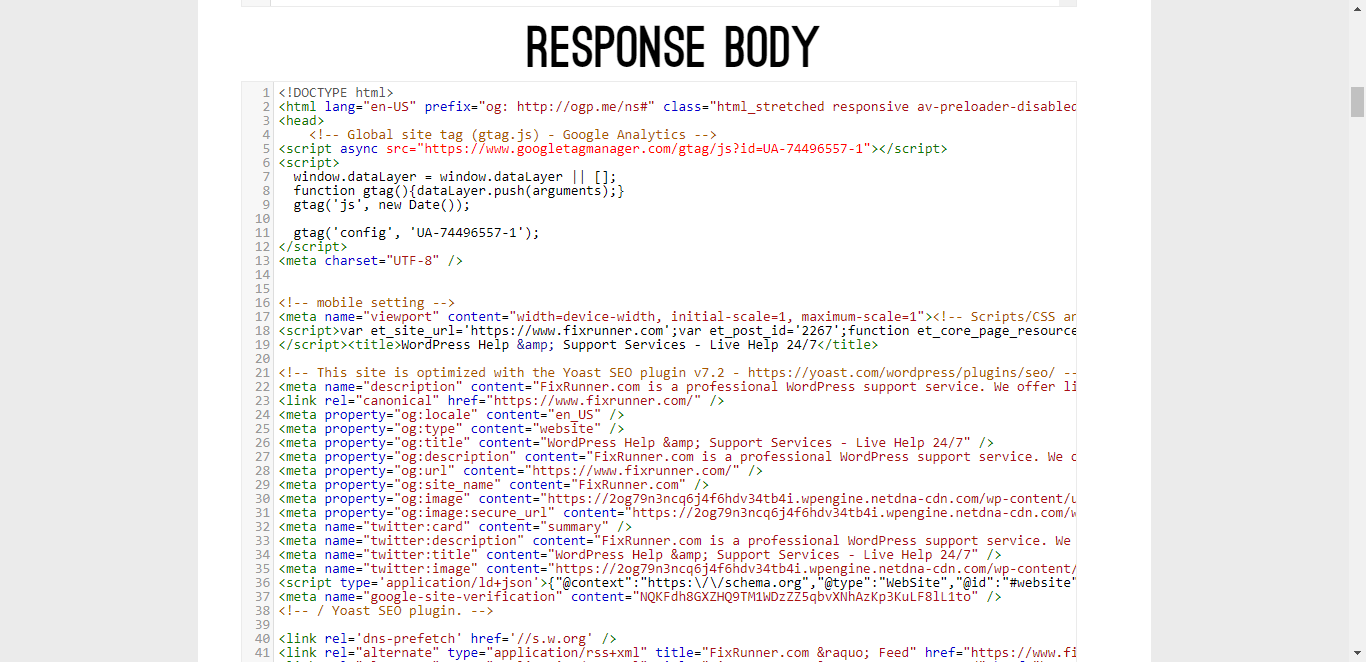
When the SQL download completes, open it in a notepad. This is where we will search for malicious code.
What Do You Search For?
To successfully scan WordPress database for malware, you should search for the two main indicators of DB malware infection. These are 1) PHP functions that are commonly used by hackers (easily exploitable), and 2) unknown links, iframes, and code sections found in your site.
1. Easily exploitable PHP functions
There are a number of PHP functions and commands that hackers highly utilize. These functions are not bad in themselves and programmers may sometimes use them ethically. However, because they are easily exploitable by hackers, if you see them in your database, there’s a very high chance that it is infected.
These functions include:
- base64_decode: This function is used to decode data encoded with base64. Since WordPress is open source, it is very unlikely to contain encoded information. This function in your DB would usually indicate that a hacker is trying to hide or mask their malicious code.
- What you should search for – “base64_decode( ” or “base64_decode (” – second one has a space before the opening bracket.
- gzinflate: This function is used to decode (inflate) data that is encoded (deflated). Same as above, an open source platform should not contain encoded sections. Presence of this function thus points to a hacker trying to hide their activity.
- What you should search for – “gzinflate(” or “gzinflate (”
- eval: This language construct tries to process any string as valid PHP code. Because this construct is very dangerous, php.net discourages its usage, and most programmers avoid it. If you find this construct in your DB, it is very likely infected.
- What you should search for – “eval(” or “eval (”
- error_reporting(0): When the zero parameter is used for this function, code errors will neither be displayed nor logged. This usage is very unlikely in any web application. If found, this may indicate a hacker testing out various codes but hiding the error reports so the site owner does not find out.
- What you should search for – “error_reporting(0)” or “error_reporting (0)
- shell_exec: The shell is the layer in a Unix operating system that processes commands. Using the shell_exec function, hackers can execute commands at the operating system (server level). Since this enables them to take over an entire server, it is a prime target for hackers.
- What you should search for – “shell_exec(” or “shell_exec (”
This is not an exhaustive list. You may research other PHP functions that commonly hackers use.
2. Unknown links or iframes in your website
Aside from the known functions, you can look at the content of your site to determine other items to search for. Often, you will find malicious iframes and redirect links if your site is infected. You can fish these out by examining your website code.
If you suspect your site is infected, it is best to display and review your code using cURL. This helps you avoid further spreading the malware to your computer or other servers.
One easy tool you can use is Online cURL. Input the URL of your site (https and all) in this tool and hit Enter. Online cURL will display your site source code.
Carefully search this code for suspicious text. You may search and review all “iframe” tags and content since hackers often use them.
Generally, to scan WordPress database for malware, search for HTML sections that are out of place in your site. For example, if your site is about airplanes and you see a section with links and information about pharmaceuticals, that’s a red flag.
During your search, note down all iframes, links, and HTML sections that you find suspicious.
Searching the DB export
First, search within the exported SQL file for the easily exploitable PHP functions we have identified. Use the exact text in quotes after “what should you search for” (see above).
Next, if you identified some suspicious iframes, links, and other text from your code review using cURL, search for these in the DB SQL export.
If you find any of these in your database, it is very likely infected.
Cleaning Up Your Database
If your search reveals that your database is infected, you would need to take steps to clean it. Our recommended method is restoring your DB to a time before the infection. If you had automatic backups running, you can do this quite easily. Otherwise, you would need to contact your web host for help.
The second option is searching for the identified malicious links, iframes, or functions in your DB and removing them.
To do this, you need to have some advanced knowledge.
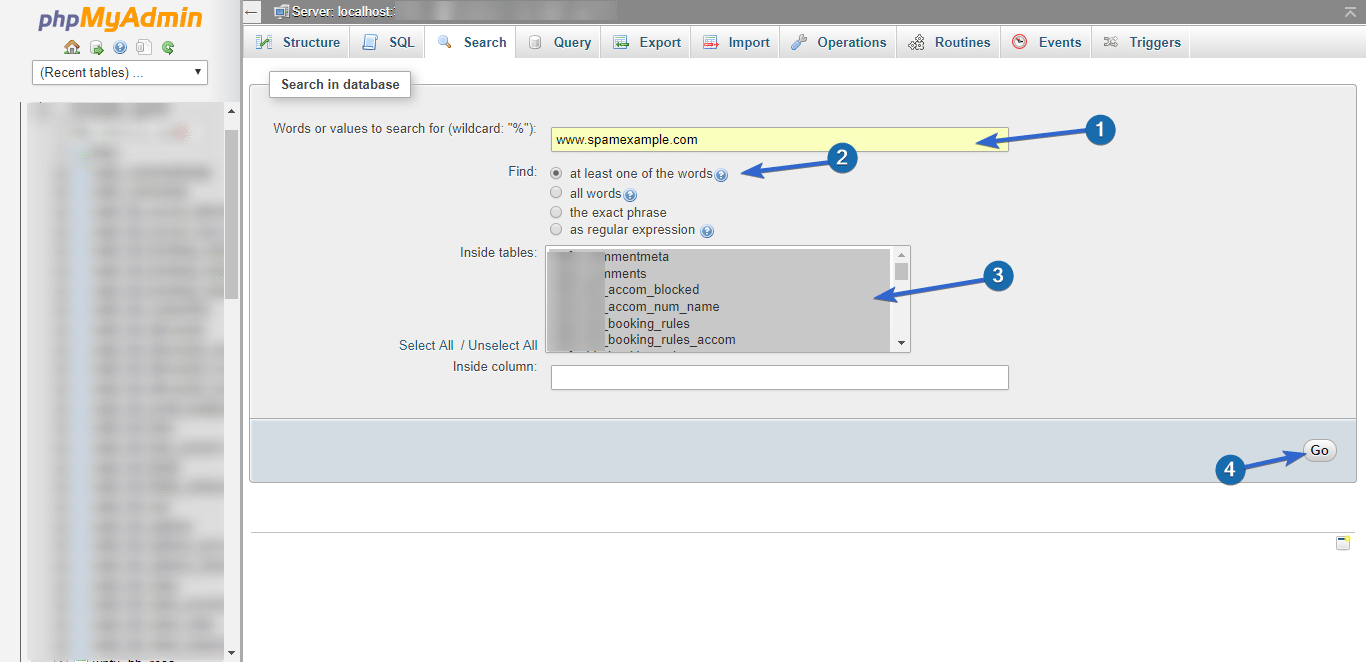
Using search in PhpMyAdmin, you can search for records containing any of the malicious code you identified. Let’s say you saw a link to “www.spamexample.com” in your site; here’s how to search for it.
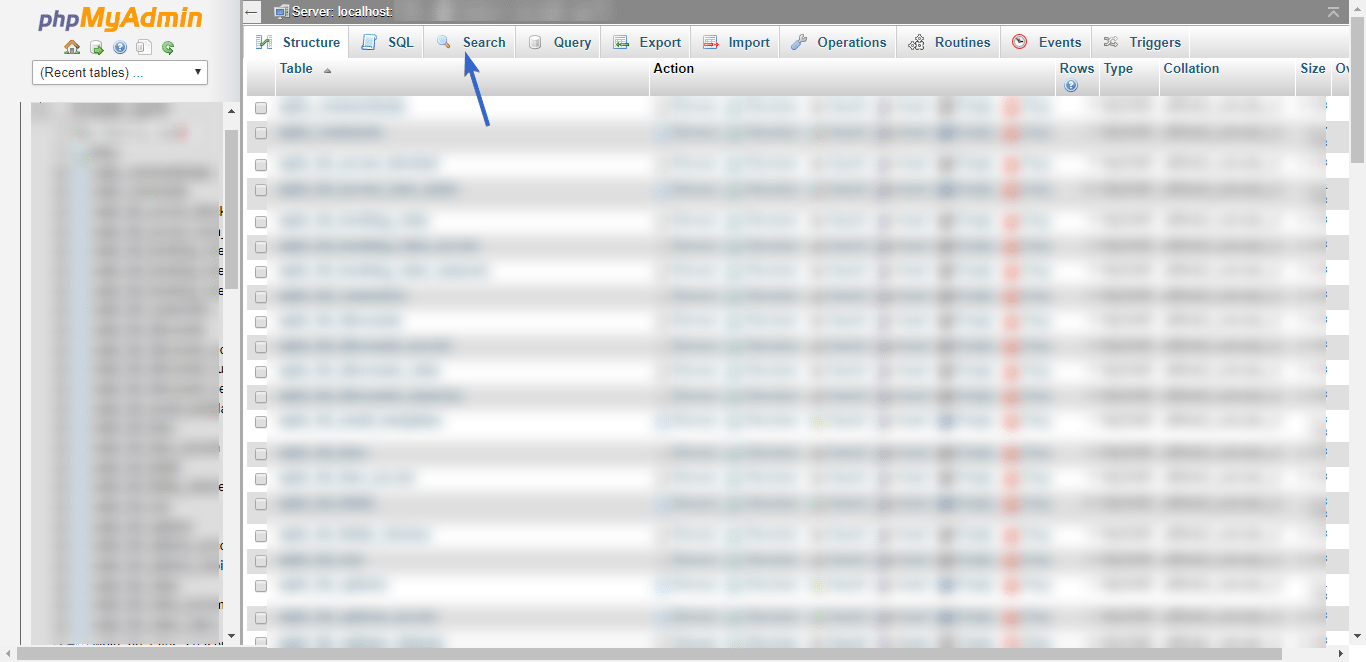
In PhpMyAdmin, click Databases and click on your WordPress database to select it.
Next, click Search.
Enter the search text in the “Words or Values” input box. Leave “Find” set to “at least one of the words”. In the “Inside Tables” input, ensure that you select all the tables. Click Go to perform the search.
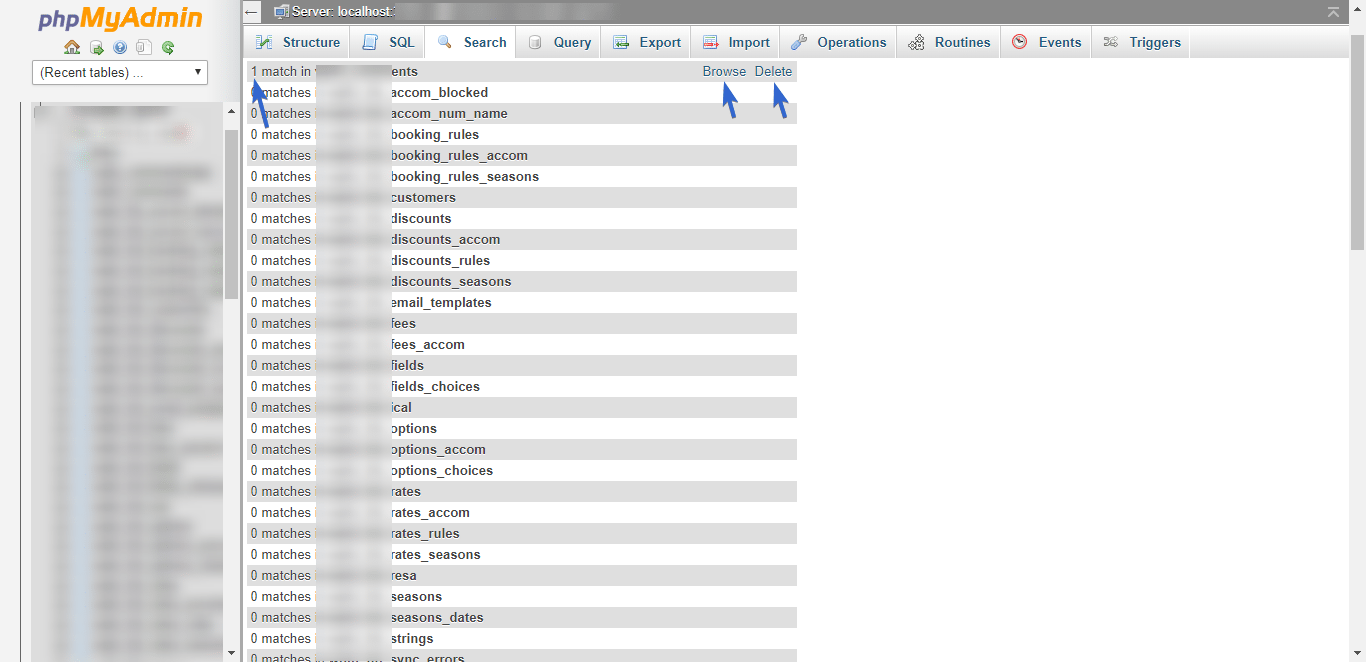
In the search results, wherever a match shows up, you have the option to browse to, or delete the record.
Click Browse to view the record. You can then decide either to edit out the malicious text, or better yet, simply delete the record.
Repeat this for every malicious text you found in your search.
Scanning with WordPress Security Plugins
As an alternative to manually searching your Database, you can check for malware by using WordPress malware removal plugins that offer database scanning.
Some plugins identify and delete malware. Others return a report of suspected malware – giving you the option to delete those you confirm as malware.
Here are three plugins you can use for DB scanning:
- MalCare WordPress Security

MalCare is a complete malware cleaning solution that will not only clean your website now but also run automatic daily scans to prevent future infections from happening. It has a really sensitive scanner, and it will detect even the deepest infections, but it won’t ping you with false alerts.
- All In One WP Security & Firewall
All In One WP Security & Firewall is one of the most popular plugins with DB scanning function. The DB Scanner looks for suspicious strings in core tables in your WordPress database.
- Exploit Malware Scanner
Exploit scanner is a plugin by Automattic (the company responsible for WordPress.com). This plugin scans the post and comment tables for potentially malicious code. When it finds suspicious content, it presents it back to you with a rating of Note, Warning, or Severe.
You can then decide what to delete.
How Can You Use This Information?
If your database is infected, the steps covered in this guide can help you identify malware, and clean up your database.
Whether you choose to use the manual search or the plugin option, please take care with what you delete. If not sure, Google it first.
To further ensure your WordPress core files and other content are properly cleaned, we suggest you read our 6 most effective WordPress malware removal plugins article.
[thrive_2step id=’36527′]Remove your WordPress malware by professionals. Check our limited time offer here![/thrive_2step]
In it, we have listed the best plugins to detect malware in WordPress files – including WordFence Security plugin, Quttera Web Malware Scanner, Sucuri Security and Sucuri Sitecheck Scanner (which offers remote scanning), etc.
We also recommend you check our WordPress security guide to secure your website properly, after you get rid of malicious code and malware. This guide provides security tips and guides to help protect your site from malware, hack attempts (such as brute force attacks), SQL injection (such as base64 code injection), etc.
Are there other steps you have used for malware scanning within your database? If yes, please share them in the comments below.
[thrive_leads id=’27346′]