WordPress Vulnerabilities (And How to Fix Them)
WordPress Vulnerabilities
Years ago, we could send information from one place to the other without worrying our heads about security. The case is different now. The internet is full of hackers seeking to break into any vulnerable website.
It even became worse with COVID 19. Workers needed to work from home, thus depending on the internet. More WordPress sites were hacked during this period.
Is it enough reason to discard WordPress as your CMS? No! A few precautions and fixes here and there are all you need.
Content:
- Common WordPress Vulnerabilities
- Common WordPress security attacks
Common WordPress Vulnerabilities
Before a thief breaks into a property, they observe. They search until they find a loophole. Then, they attack.
This is the way it is with your WordPress website, your online property. There are cybercriminals waiting to dig their claws into your website.
They have sophisticated tools through which they locate vulnerable websites. Then, they exploit those weaknesses. The least you can do, as a site owner, is tighten all loose ends.
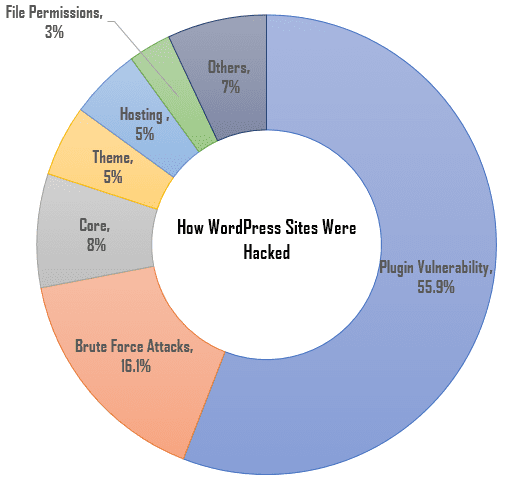
Based on a survey by WordFence, most WordPress attacks were as a result of plugin and core vulnerabilities, brute force attacks, poor hosting, etc.
As much as possible, ensure your website has no passage through which cyber thieves hack WordPress sites. Alternatively, you may get Fixrunner to help you harden the security on your website. It saves you all the stress.
Nulled WordPress Themes and Plugins
Some websites distribute premium themes and plugins for free or at a cheaper price. Hopefully, you aren’t thinking it is an act of charity because it isn’t.
Nulled WordPress Themes and plugins often contain malicious code and backdoor access that compromise your site’s security.
They grant hackers access to steal your data, advertise illegal stuff, deface your website, use up your server resources, misdirect your readers, and eventually bring down your website.
As the saying goes, “when you buy cheaply, you pay dearly”. Using a nulled WP plugin or theme costs you more in the end.
Outdated WordPress core, Plugins and Themes
The most secure version of WordPress is the latest one. This is because updates are meant to add new features and to repair flaws in previous versions.
A good number of hacked websites were as a result of outdated plugins, themes, and WP core software. Update them to keep your website safe.
Weak Password and Usernames
Your WordPress login page is like the gateway to your website. You must reinforce it with strong passwords and usernames. Passwords like ‘123456’, ‘admin’, or ‘password’, are easy to break. Instead use a long, rock-solid password containing upper and lower case alphabets, numbers, and symbols. You may use two-factor authentication to strengthen it further.
Also, the default WordPress username (admin) is a generic one. Even a fifth-grader can get it correctly, talk more of a hacker with sophisticated tools. Change it to a stronger one.
Poor Hosting – WordPress Vulnerabilities
Quite a number of WordPress security issues are a result of poor WP hosting.
To run your WordPress site effectively, a web host must support HTTPS, PHP version 7.4 or greater, MySQL version 5.6 or greater OR MariaDB version 10.1 or greater.
Anything short of these could open you up to security issues.
Not using SSL certificate
Sites without SSL do not encrypt data sent between browser and server. This means your data can easily be stolen. Using an SSL certificate encrypts your connection and prevents hackers from laying hands on your data. On average, an SSL certificate costs $12/year.
Weak WordPress User role practices
There are 5 user roles in WordPress: Administrator, Editor, Author, Contributor, and Subscriber. Anyone with Administrator privileges has unrestricted access to do anything on the website. They can create and edit posts and pages, modify themes and plugins, and even delete other users.
You should never make just any user an admin. They could take advantage of the privilege and ruin your website.
Most Common WordPress Security Attacks
WordPress attacks come in different forms. Here are a few of them:
SQL injection
In this form of attack, hackers have their eyes on your database (this is where WordPress stores your data). They exploit vulnerabilities in the input fields of contact forms and then inject malicious code into your database. There are two forms of SQL injection vulnerabilities:
In-bound SQL injection – The intention of this kind of attack is to steal data from a victim’s database.
Blind SQL injection – Its intention is to delete content from a victim’s database and eventually bring down the website.
How to prevent and fix SQL injections – WordPress Vulnerabilities
If you notice a sudden spike in emails from your contact form, and errors on some of your site’s pages, it may be an SQL injection attack. The ideal thing to do is to scan the database for malware. You can do this with a WordPress security vulnerabilities scanner.
Also, since this attack is primarily a result of plugin vulnerabilities, you should run a general site scan to fix any issues.
Cross-site Scripting XSS – WordPress Vulnerabilities
This is one of the most common forms of attack and is also known as a Cross-site Scripting vulnerability. It involves injecting malicious code into a victim’s browser. The intent is to collect visitors’ data and even redirect them to dangerous sites.
Reflected Cross-Site Scripting vulnerability: This is the most common type of XSS. In this attack, a malicious code is added to a legitimate site’s URL. Then, when a victim loads the link, the browser loads the injected code as well.
Stored Cross-Site Scripting vulnerability: This occurs when a hacker adds a comment on a website and injects a malicious code. Anyone who clicks on it falls victim.
How to Prevent Cross-Site Scripting XSS attack
To help prevent XSS attacks, there are a couple of things you can put in place. First, stop users from posting HTML on your site, either via comments or otherwise. You can create rules that hinder users from entering data that doesn’t meet certain criteria into a form.
You may also use the Prevent XSS vulnerability plugin to help you prevent such an attack.
Pharma Hack
This is also a result of plugin and theme vulnerabilities. In this form of attack, hackers target your ranking posts and pages. Then, they project spammy ads and keywords to advertise their products.
How to Prevent and Fix Pharma Hack vulnerability in WordPress
The easiest way to prevent this attack is to use only credible themes and plugins. Also, update them when the need arises.
Brute force Attack – WordPress Vulnerabilities
This is a form of attack where a cybercriminal guesses your password/username combination until they get it right.
Usually, these hackers have powerful tools through which they try hundreds of possible passwords in a few minutes. Coincidentally, WordPress permits an unlimited number of failed login attempts. So, they can try for as long as they need to get it right.
Even if they do not succeed, several logins may take its toll on your server.
How to Prevent a Brute Force Attack
You can avoid Brute force attacks by limiting login attempts. The Limit Login Attempt Reloaded plugin could help you do that. Simply, download and install the plugin on your website. Anyone who attempts to login multiple times will be locked out (temporarily). This procedure is enough to discourage malicious hackers.
Furthermore, you should never use simple passwords. Use a password that has a combination of numbers, symbols, capital, and small letters. Also, use two-factor authentication to add an extra layer of security.
Other security vulnerabilities include privilege escalation, Phishing, Pharma hack, Japanese Keyword Hack, etc.
What Next?
Armed with this knowledge, you won’t be caught unaware anymore.
Make sure to use a good WordPress security plugin, have a WordPress backup, use the latest WordPress version, and update themes and plugins regularly. You should also avoid using tools resources from dodgy sources. If you get something premium for free, it may end up costing you more.
To learn more about hardening your site against security threats, read our WordPress Security Guide.
More Resources
- Best WordPress Security Plugins To Stay Protected
- How To Fix Common WordPress Errors, Problems & Issues
- How to Block IP Address in WordPress